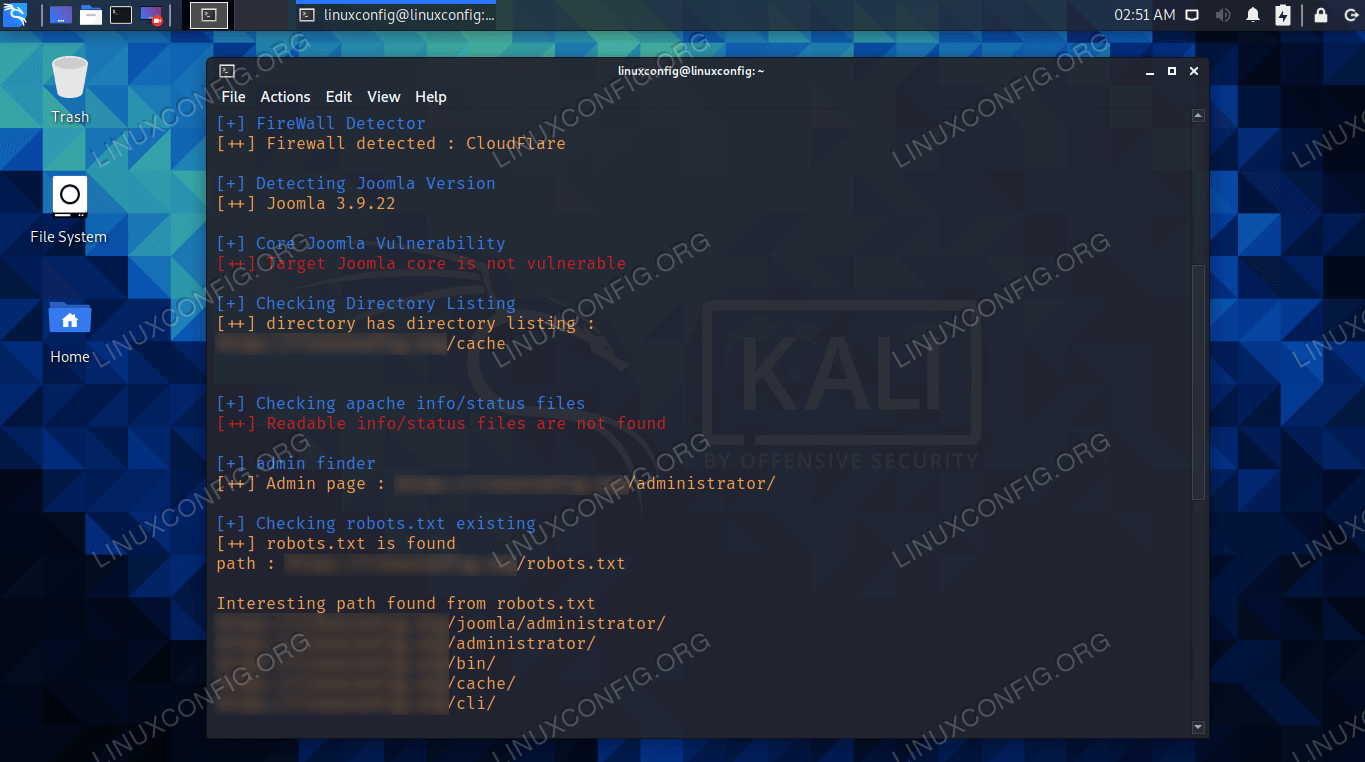
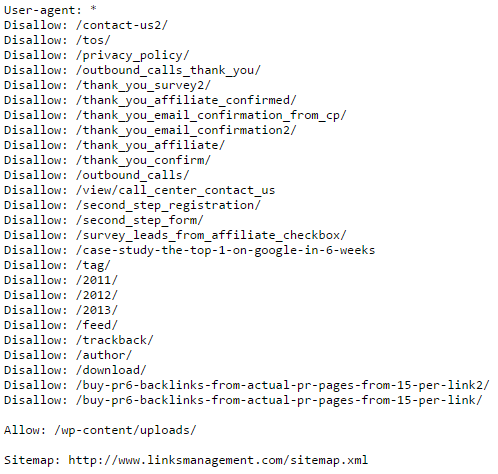
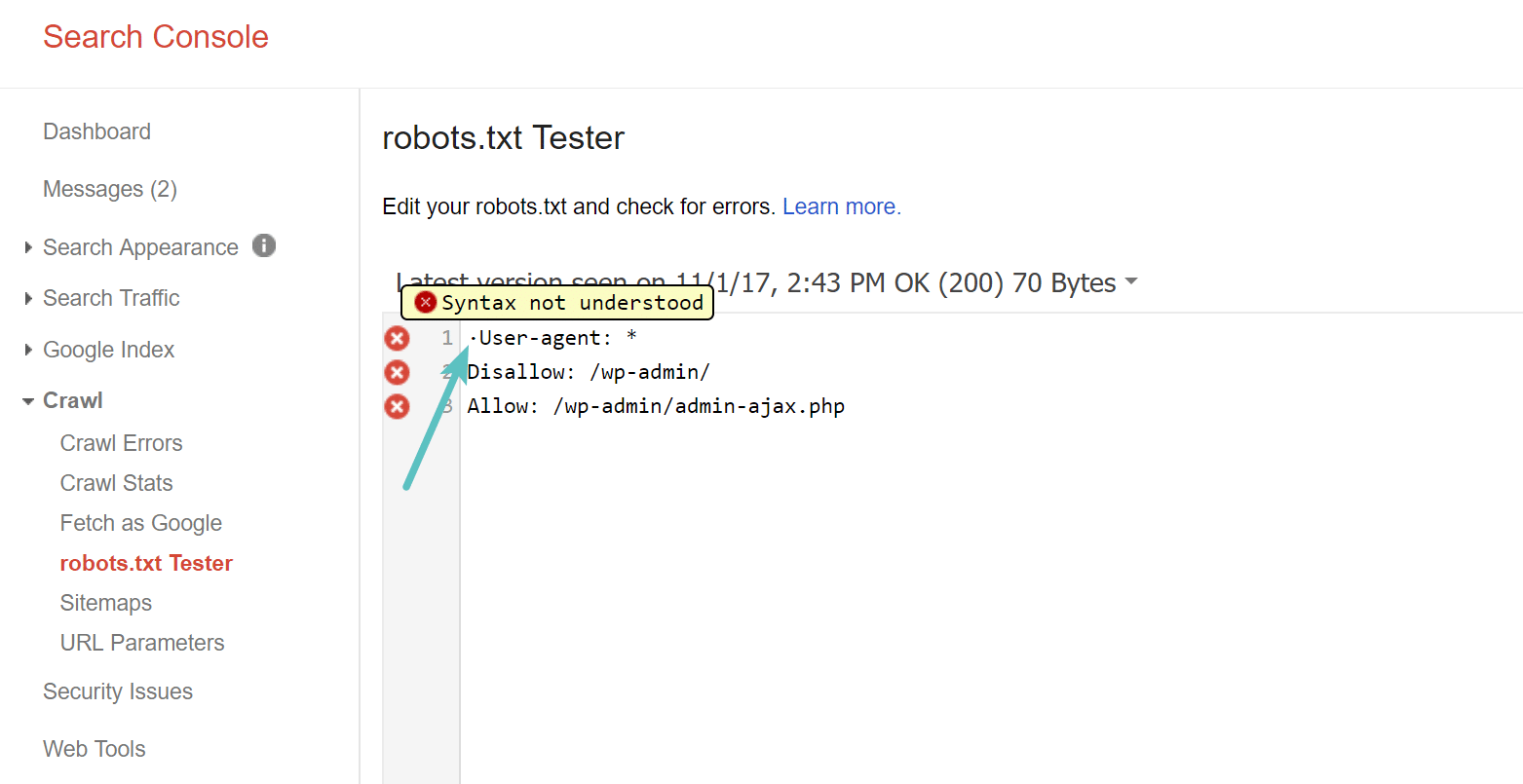
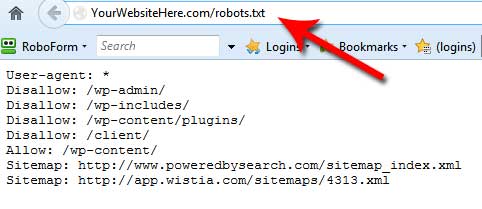
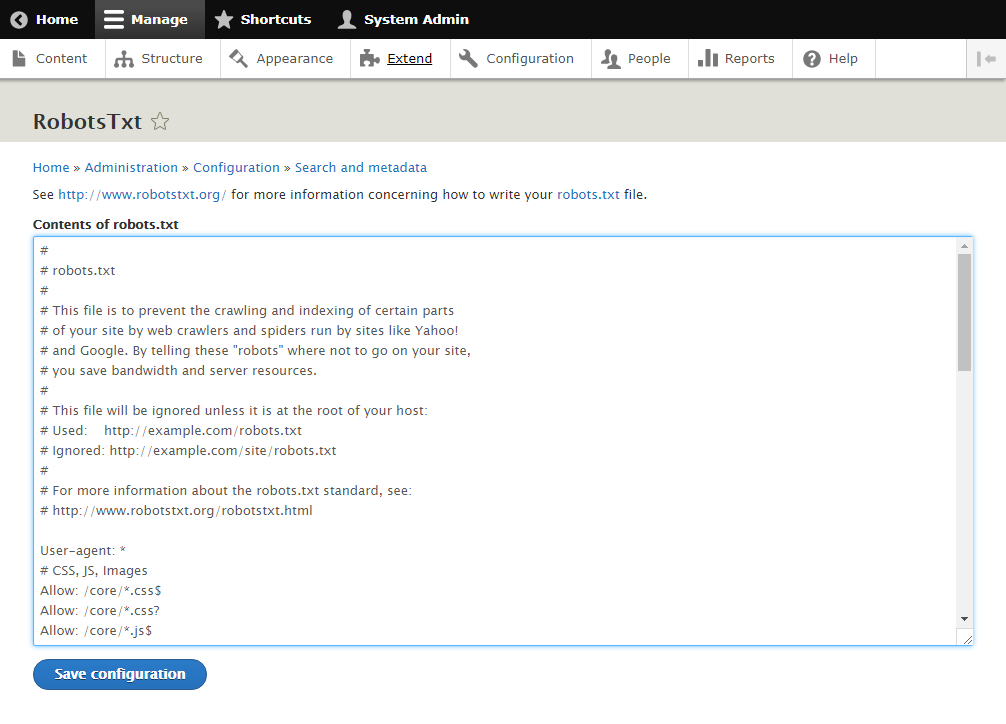
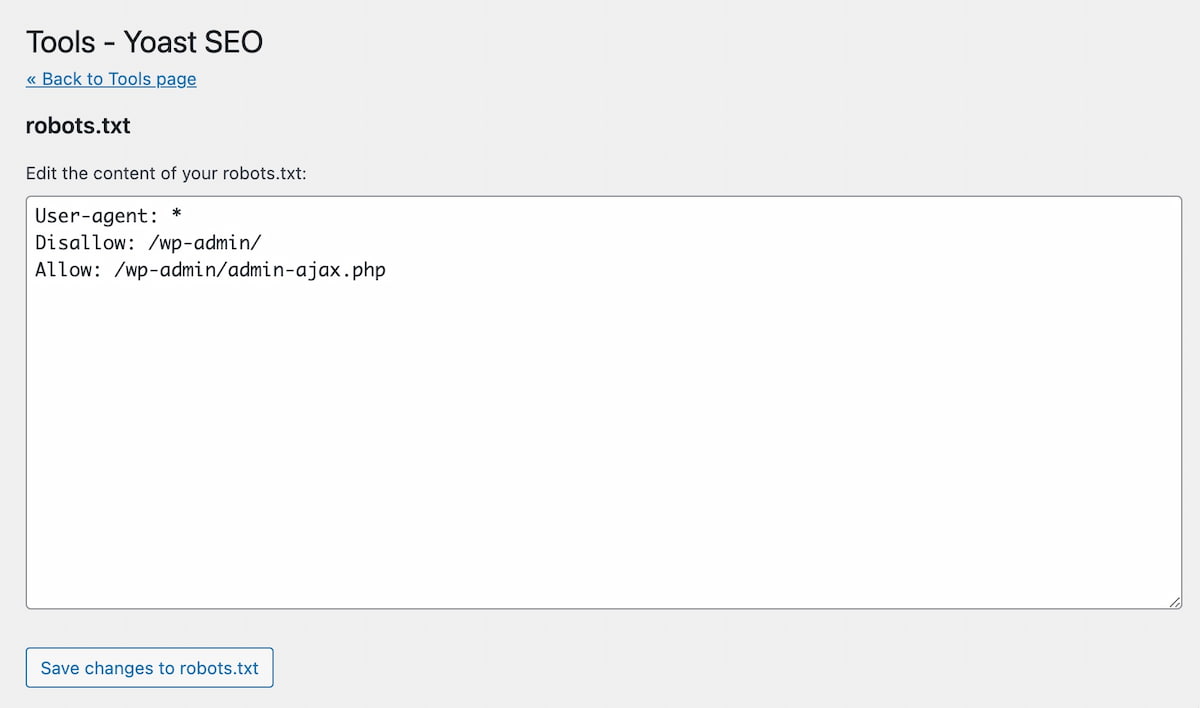
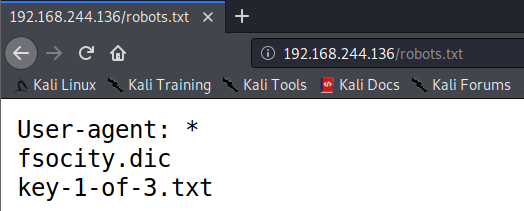
WordPress Plugin WordPress Robots.txt optimization (+ Multisite)-Website traffic, ranking & SEO Booster + Woocommerce Security Bypass (1.2.5.1) - Vulnerabilities - Acunetix

Sophos on Twitter: "The concept of begging for a reward for innocuous or meaningless reports (aka "beg bounty") appears to be reaching a fever pitch. This growth appears to be fueled by