Icon security system, information data protection privacy, vector shield with closed lock, personal data protection concept Stock Vector Image & Art - Alamy

Dell study finds most organizations don't think they can recover from a ransomware attack - TechRepublic
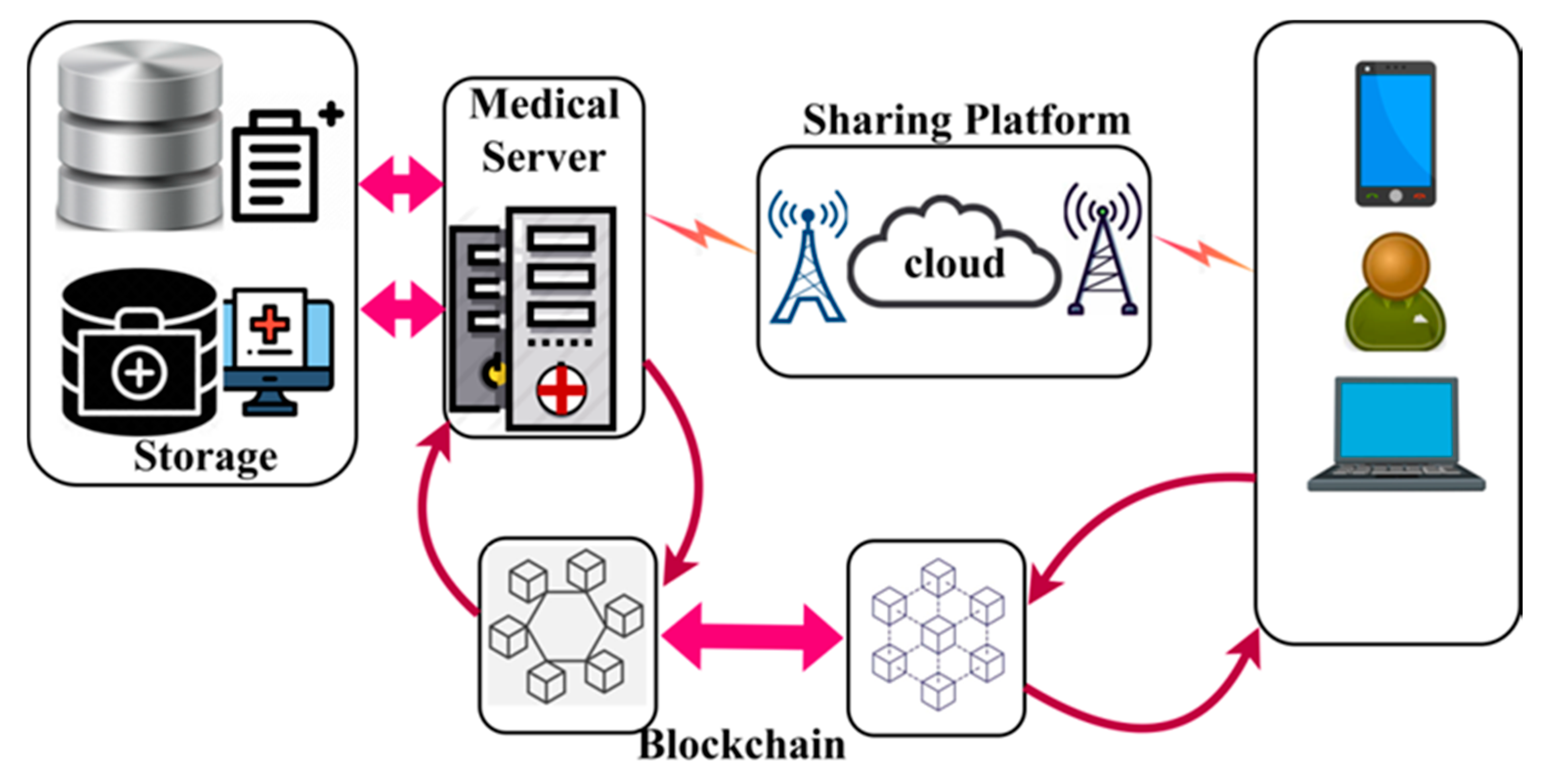
Healthcare | Free Full-Text | Enhancing Privacy and Data Security across Healthcare Applications Using Blockchain and Distributed Ledger Concepts


![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/10/Data-Privacy-vs.-Data-Security.png)





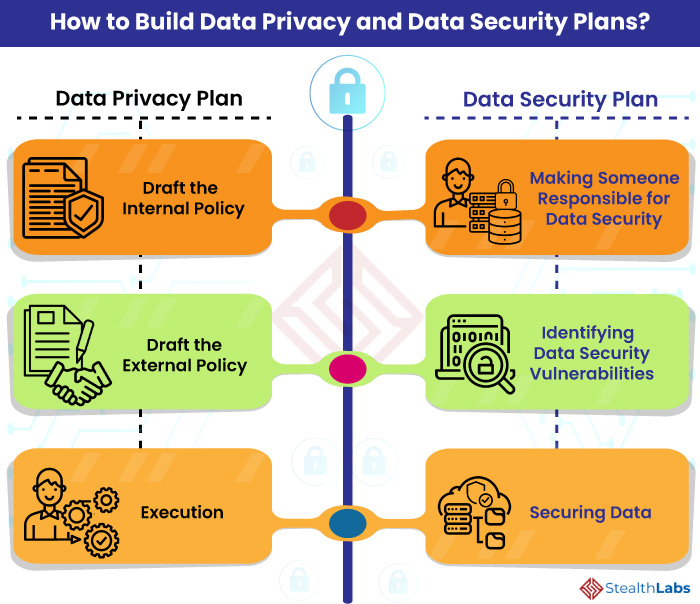

![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2020/08/visual-representation-of-data-privacy-and-data-security-areas.png)